If you register a domain name on Gandi.net, you’ll get a free Standard SSL certificate from them for a year. The best part is you don’t have to apply for the SSL certificate right away, you can apply it anytime during the first year of your domain name registration.
So yesterday when I realized 1fix.io (which is registered with them) will be renewed in about a month, it just came to me I haven’t got a SSL certificate for my site, and now it’s about time.
The process is easy, you just log into your Gandi account, purchase a Standard SSL certificate, when checkout, the amount will be discounted to 0 if you haven’t purchased one for your domain. That means the first year (starts from the day you purchase the SSL, not the domain) will be free, and $16 per year thereafter.
Basically I followed all steps from Julien’s post: Nginx #1: Set up Gandi Standard SSL Certificate, even I was pretty sure that I got everything right, I still can’t get the SSL work with Firefox, it took me hours to find the solution.
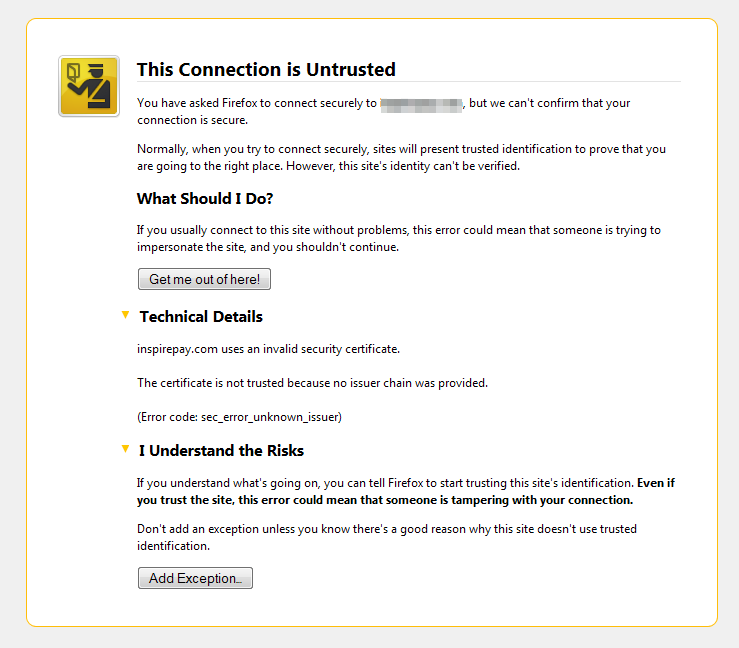
The notorious “sec_error_unknown_issuer” error in Firefox
After all steps got done, I can browse 1fix.io with “https://” in Chrome, it just worked like a charm. But when I open Firefox, I saw the last screen I’d like to see – “The Connection is Untrusted”:
I hope it was a cache problem or something, but it’s not. Clean up the cache in Firefox didn’t help. So I went to Google. From the search result, I learnt a term “issuer chain“. Other browsers, like Chrome, IE, Safari etc., they’ll download the certificates from all issuers in the chain for users on the background, but Firefox won’t. So we need to combine all certificates manually by ourselves, if we don’t want to scare away the users come from Firefox.
Always check the official documentation first
A great lesson learnt here, is you should always check the official documentation first. In this case, Gandi has a wiki page to show me how to Retrieving the Gandi Intermediate Certificate, but I just ignored the link (don’t know why, maybe it’s 1 AM and I’m tired).
In the wiki, I realized I need to combined 3 certificates into 1 crt file as ssl_certificate for Nginx, and the order should be like:
- crt Gandi generate from my CSR (the Standard certificate from Gandi)
- intermediate Gandi certificate (PEM format)
- the Root CA for SHA2 certificates from USERTrust
Finally, Firefox loves the new https://1fix.io.
Be sure you’ve disabled the SSLv3 on Nginx
The POODLE still bites if you don’t disable the SSLv3 protocol. A very useful link for you is How to Disable SSLv3, you can find anything you need to know to disable SSLv3 on your servers. On Nginx, with one line in your server or site config:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
And restart the nginx server. You can be safe (for a while).
Allow connection on port 443
This afternoon when I was at my parents’ place, and tried to log into my site to write this post, the site seemed down. I took some time to figure out, my site has been down for… about 10 hours, after I set up the SSL certificate and redirect all connection to HTTPS.
My own IPs are in the whitelist so I can browse the site from my place. Stupid me forgot to allow connection on port 443, and I won’t find it unless I left home.
Embracing HTTPS
There’s an article on New York Times illustrates benefits of HTTPS. Besides security, improved ranking in search engines should be the best reason to encourage people (clients) to get their own commercial SSL certificates.
Parttime bloggers like me always go for cheap SSL certificates under $30 a year, and most of them will bump into the “sec_error_unknown_issuer” either. I hope this article can be helpful some day, and even it’s not, I still enjoy to publish what I learn.
Happy weekend!

Leave a Reply